Not so long ago when an industrial plant operator needed to redirect flows or even start and stop a procedure, it was often times a long and arduous process of turning valves, painstaking sequences, and long trips from area to area within a plant or facility with a handheld radio. While there are still facilities that might require this type of manual operation, the landscape has significantly changed, with the introduction of supervisory control and data acquisition (SCADA).
While all of this control and operational stability has benefitted the global industrial process as a whole, what happens when the control and data are compromised or even lost? Will we have the ability and the sheer manpower to physically achieve and complete the many steps and processes within industrial facilities or plants that have now been taken over and controlled by the massive computer systems designed to control and acquire data through a system such as SCADA? Therein lays the question or perhaps the difficulty.

Photo 1. The QATAR National Control Center is a highly sophisticated example of how SCADA can be used for control of systems and the data acquisition from those systems as well.
Our Journey
In this article we will look at how this relatively new control technology has changed the industry forever, and has placed the control and data of many complex processes at the operator’s fingertips. We will visit the NEC and see what guidance it has for us and the requirements we need to adhere to when considering and installing SCADA systems. And we will look at what’s on the horizon with regard to Homeland Security, Article 708 – Critical Operations Power Systems (COPS), the overall security of SCADA systems, and how it is all integrated into the mix.
A Little History
Supervisory control and data acquisition (SCADA) systems have become a critical part of the landscape of late, silently and methodically marching forward, providing the vital infrastructure for a new industrial revolution. Not only have these systems been proven to save time and to provide economic benefits, the new operational flexibility that is now gained by SCADA can have enormous benefits when it comes to safe control of systems and data that can be viewed about any process instantaneously.
Long gone are the days when industrial plant operators jumped in golf carts and were aided by maps of industrial pipeline drawings to figure out which valve to open or close and at what stage of the process. Not only was this dangerous, it was very inefficient and costly, requiring many men and a lot of time.
While the process world grew and perfected these systems, additional elements were born, digital control systems (DCS) and programmable logic controllers (PLC), to further enhance this supervisory control and data acquisition. With this trifecta, if you will, we now have all the control we need to speed up, and safely conduct these processes and increase production to supply the demand of goods and products for a hungry nation.
Can we use these requirements?
The requirements for SCADA systems reside in the informative annexes of the NEC, in Annex G.

Photo 2. SCADA today is a complex system of computers, PLCs, and high-speed communication to accomplish the many tasks that are necessary for safety and efficiency.
While it is not part of the requirements of the NEC, it has been included for informational purposes, as well as adoption. Conversely, if an informative annex is referenced in the body of the NEC, such as Annex C – Tables, then it becomes part of the NEC by reference.
SCADA, the NEC, and Critical Operations Power Systems (COPS)
The requirements for SCADA systems have incorporated Homeland Security requirements by the integration of Article 708 – Critical Operations Power Systems (COPS) into Informative Annex G.
This provision among others is to ensure that a SCADA system for the COPS loads is completely separate from the building management SCADA system.
Informative Annex G – (A)(2) General – requires that when a SCADA system is employed “no single point failure should be able to disable the SCADA system.”
We also see in Informative Annex G – (A)(3) General – what the SCADA system is permitted to control. This section indicates that the SCADA system cannot only control and monitor mission critical electrical and mechanical systems, but other systems as well. These systems include but are not limited to (a) the fire alarm system, (b) the security system, (c) power distribution, (d) HVAC and ventilation [damper position, airflow speed and direction], (f) load shedding, and (g) fuel levels or hours of operation.
Planning and the NEC
Before the installation or deployment of a SCADA system, proper planning needs to be done. Informative Annex G – (A)(4) General – requires that an operation and maintenance analysis, as well as a risk assessment be completed to provide maintenance parameter data, prior to installation.
One should also notice that if a redundant system is provided for backup, there are also requirements.
Informative Annex G – (A)(5) General – indicates that if a redundant system is employed, it shall be in either warm or hot standby mode at all times.
Open Protocol
When a SCADA system is employed not only does the NEC tell us in Informative Annex G – (A)(6)that the controller must be a programmable logic control (PLC) , Informative Annex G – (A)(7) requires that the SCADA system must utilize open, not proprietary, protocols.
Damage Assessment and Graphical User Interface
In the unfortunate event of a system failure or problem, Informative Annex G – (A)(8) General – informs us that the SCADA system is required to not only assess the damage to the facility, but to also determine system integrity after an event.
The actual monitor display itself is required to have a graphical user interface that will allow the user to readily recognize all major components that are being monitored as well as controlled by the SCADA system, with easily discerned color schemes as identified by Informative Annex G – (A)(9) General.
Storage of Critical System Parameters
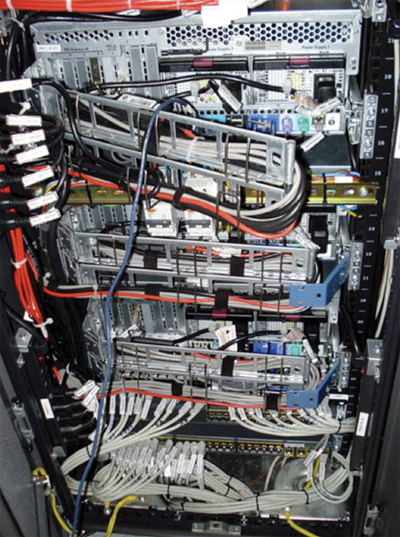
Photo 3. SCADA real time automation controller (RTAC)
To round out the general requirements for SCADA it is indicated in Informative Annex G – (A)(10) General – that the system shall have the capability to provide storage of critical system parameters for at least 15 minutes or more, if an out-of-limit condition exists anywhere within the system. This data is also to be stored off site at a separate secure data storage facility located off site.
SCADA systems and the Power Supply
Informative Annex G – (B) Power Supply – lays out the requirements in the NEC to ensure that the power that is being provided to the SCADA system itself is well-protected, not subject to failure. In addition to the regular power supply, a direct-current station battery system, rated between 24 and 125 volts dc, and capable of 72 hours of sustainment is the very minimum allowed.
All of the batteries supplying the SCADA system will be required to be completely separated from batteries of other electrical systems.
All SCADA system power supplies are required to have a properly installed surge protection device (SPD) at its terminals with a direct low-impedance path to earth, as well-protected and unprotected circuits are required to employ physical barriers to prevent coupling.
Security and SCADA
Informative Annex G – (C) Security against Hazards has six criteria that are required to be adhered to in the effort to prevent the SCADA system from becoming adversely affected.
Controlled physical access by authorized personnel to only the system operational controls and software is to be provided.
The SCADA systems and its components are required to be protected against dust, dirt, water, and other contaminants by appropriate encloses for the environment served.
Conduit or EMT cannot violate the integrity of the SCADA system enclosure.
The SCADA systems are required to be located in the same secured locations as the systems that they are monitoring.
The SCADA system is required to be provided with a dry agent fire protection system or double interlocked pre action system using cross zoned detection, to minimize the threat of accidental water discharge into the unprotected equipment. The fire protection system is also required to be monitored in accordance with NFPA-72 The National Fire Alarm and Signaling Code
SCADA systems are not to be connected to other network communication systems outside the secure location without encryption or the use of fiber optics.
Are we safe yet?
While we hope that these new provisions in the NEC, born from the Homeland Security Act, are enough to at least fend off threats to our national infrastructure, there are those who work tirelessly to develop the means to cripple us with devices such as electromagnetic pulse (EMP) and high-powered microwave (HPM) that can adversely affect SCADA systems and create havoc in a moment’s notice.
Maintenance and Testing of SCADA systems
For any system to work properly maintenance is required. Informative Annex G – (D) Maintenance tells us that a documented preventative maintenance program is required to allow the testing, troubleshooting, repair, and/or replacement of a component or subsystem, while redundant components or subsystems are actually serving the load.
SCADA systems require periodic testing under actual and / or simulated contingency conditions. The reader can find the testing requirements and intervals in NFPA 70B Recommended Practice for Electrical Equipment Maintenance.
What have we learned?
Not only have we visited the industrial facility process and have seen how SCADA systems have revolutionized the industry across the board, we have seen that the NEC has many very important requirements that need to be adhered to that will ensure the safe, efficient and long-term operation of a SCADA system. We have also looked at the added security and system processes that are now required to avoid the possibility of our vital national infrastructure from coming under attack from those who would promote chaos and civil unrest.
The accelerating penetration of SCADA systems, along with their electronic cousins, digital control systems (DCS) and programmable logic controllers (PLC), as critical elements in every aspect of every critical infrastructure in the Nation, is both inevitable and inexorable. While conferring economic benefit and enormous new operational agility, the growing dependence of our infrastructures on these omnipresent control systems represents a new vector of vulnerability in the evolving digital age of the 21st century, such as cyber security.











Find Us on Socials